Internet Banking. OK, Of course that's very secure. Your Bank, your Browser and a TRUSTED 3rd party have ensured that you will get a secure session for your login (Username and Password) and your banking activities. Called an SSL (Secure Sockets Layer) session, you also get visual cues from the browser like the good old PADLOCK and in Internet Explorer, a nice green address bar. [IT experts/geeks are allowed yawn at this point and their eyes can glass over a bit - but keep reading!]. The URL will start with https://..... where the 's' means your connection is secure based on a session key and trusted 'certificate' (issued to the bank / ISP etc.) and a pre built-in matching public certificate in your browser.
Web based Email. OK, lots of these around. Gmail, Hotmail (Windows Live), Yahoo etc. Most of these systems log you on using SSL and your Username/Password is safe & secure from naughty people that try and intercept your data.
Being a cool switched on person you have a cute Username (like VarthDader) and a WOW-eee super-duper password no one would ever guess in a billion years.
So, you also use this login for your ISP email, You probably use Microsoft Outlook or Outlook Express. Perhaps Eudora or Thunderbird. There are quite a few cute email programs out there.
We are now getting close to the point where I let you know about one of the best kept secrets of the Internet email login process used by 99% of ISP's. Called the POP3 Protocol (Post Office Protocol Version 3).
[IT Geeks can stop yawning now, also put your drink on the table in case you spill it when you (from shock) suddenly understand the seriousness of what you are about to read. Also remove chewing gum as we don't want you choking as you 'gasp'].
OK, here it is: In the default settings used by all Email programs (using POP3), your Username and Password are sent over the network in plain text!!
This occurs EVERY time you push Send/Receive or probably-typically every 5 minutes if you are auto checking your email.
So, you are shouting to the world "VarthDader" (Not too much of a problem there) BUT you are also shouting "Get$%1289offmefecdblah" (That was your top secret password)!
Do I have your attention now? :-)
First classical textbook response to this news is DENIAL, then comes anger, then depression etc. Or maybe it’s the other way around. Anyway you get the idea.
To deal with the denial skeptics who are also IT geeks, go download the FREE Network Monitor Version 3.3 from Microsoft and install it on your PC.
http://www.microsoft.com/downloads/details.aspx?familyid=983b941d-06cb-4658-b7f6-3088333d062f&displaylang=en
Being network geeks, you will soon figure out how to capture your LAN or Wireless LAN packets of data. Open a new "Capture Tab" and push the 'play' button to record the traffic. Open Outlook and check your ISP email. Now push the stop button on the Network Monitor and have a look at the raw data.
Notice your Username AND PASSWORD are there in PLAIN TEXT for all to see!!
This is why the recent Google "Open/Unsecured Wi-Fi data collection" DID possibly record personal data. Especially if you were using an unsecured wireless network and your Outlook did a Send/Receive on your POP3 account as the Google car drove past.
For non-IT geeks like mom. Trust me, you are telling the ISP and any Internet provider between your house and the ISP your Username and Password over an UNSECURE network.
So, where are we? We are red faced for starters; especially for those of us who thought we were clever:
1. Used the same login 'credentials' (Username/Password) for our online banking AND our email. We correctly took extra, extra, super special care to use secure banking. SSL with padlock, fries and 4 nuggets. OK so far - so good.
2. Are stupidly checking our email using Microsoft Outlook (or a similar program) with standard "POP3 protocol" and telling everyone (who may like to intercept our data) our Username and TOP SECRET and Password!!!! (Yes that deserves 4 exclamation marks).
Of course some IT geeks will be reading this and already know that plain text is used for POP3 accounts in the default settings mode. But, - hey guys, let's do something about that. Let's set SSL for email. Ready? Let’s go.
THE SOLUTION
------------------
In the following example we will use bigpond.com a large Australian ISP/Telco.
We will also be using Microsoft Outlook 2010 (but the settings for Outlook 2003 & 2007 are the same).
We are going to TURN ON SSL for our email. This simply involves 'ticking' one box and changing the "POP3" server from mail.bigpond.com to secure-mail.bigpond.com.
By using SSL you have the SAME SECURE LINK that you get when doing online banking. Now, no one can capture your secrets.
EASY. So, why were you not told about secure SSL when you first setup your email account? More importantly, why can't you even find out about this today on your ISP 'Help' webpages!!
The answer is simply that its too hard for your ISP. More specifically - they can't be bothered when there is an easier way. Your ISP is taking the path of least hassle. Also, if everyone actually used SSL the ISP email servers would probably struggle to keep up. But that technical issue is NOT YOUR problem. It is something the ISP needs to address.
Step 1. Open your Outlook email account settings. Find the "Incoming mail server". Using our example of BigPond as an ISP, you would see mail.bigpond.com normally.
Ok, change that to secure-mail.bigpond.com as shown below.
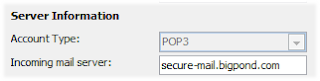
Step 2. Click on Advanced settings and check (tick) the box as shown below.
"This server requires an encrypted connection (SSL)."
THATS IT! SIMPLE!! Save your account settings, The 'test' should work just fine.
You are no longer shouting your secret password over the network in plain text. All data including your login credentials are safe from prying eyes.
OK, for other ISP's (non-BigPond) Step 2 is the same. For Step 1 you will need to discover if you need to change the name of the POP3 server. A lot of the time you won't need to change it at all.
So, for non-BigPond users, just do Step 2. And try that.
If you are using Outlook and a box pops up saying "Do you want to continue to trust.. etc. Blah blah..., click on "View Certificate" and you will see the server name that the certificate needs. Just use that in the POP3 server name as shown above in Step 1.
DONE!
Enjoy your security! Tell your friends about this blog!
